
CHALLENGE OVERVIEW
- Link: https://tryhackme.com/room/road
- Difficulty: Medium
- Target: user/root flags
- Highlights: retrieving user credentials from a Mongo DB, privilege escalation by exploiting a glitch in the
pkexecbin - Tools used:
nmap,dirb,burpsuite - Tags: pentesting, security, mongoDB, SSH
BACKGROUND
 What is black box pentesting?
What is black box pentesting?

The term black box refers to a challenge where only the target machine IP is known to the penetration tester. Nothing else about the server is disclosed to the attacker, so everything must be discovered during the enumeration stage.
On the other end of the spectrum is white box pentesting, where information about the internal workings of a server is shared with the pentester.
ENUMERATION/RECON

Let’s kick things off with some standard nmap and dirb scans.
sudo nmap -p- -A $targetIP -O -o /home/kalisurfer/THM/road-walkthrough/nmap.txt
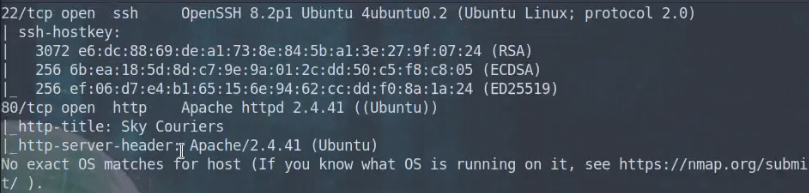
It looks like they are running SSH and HTTP services. No surprises here!
dirb http://$targetIP



Our dirb scan sniffed out a few interesting directories: /assets /phpMyAdmin/ChangeLog and /v2. We’ll look into each of these in more detail.
INVESTIGATING /phpMyAdmin
We discover a login portal at /phpMyAdmin/index.php

INVESTIGATING /assets
When we browse the changelogs, we can identify the version number (5.1.0) for phpMyAdmin.
We also find a link to a Git repo with changelogs going back all the way to the year 2000!
This is a potential treasure trove of interesting information. We’ll check exploit-db to see if there are any known vulnerabilities. There are a bunch, but nothing for version 5.1.0.
For now, let’s move on.


INVESTIGATING /v2
We discover another login portal /v2/admin/login.html. This one has a register option, so we can go ahead and create a new user and see what else we can view from within a standard user account.

INITIAL FOOTHOLD

We pivoted from our new user to the admin account by intercepting the TCP request to change the password using burpsuite and modifying the parameters to the admin’s email address before forwarding the request.
After successfully changing it to the admin’s password, we can login as admin with our new password and upload a revshell via the profile pic upload option.

From our admin dashboard, let’s go ahead and upload a revshell (from PHP pentest monkey, naming it revshell.php), start up a netcat listener on the corresponding port, and finally trigger it by loading the following address in our browser.
http://10.10.154.107/v2/profileimages/revshell.phpWe caught the revshell and now we have our initial foothold!
EXTRACTING USER CREDENTIALS FROM MONGO DB



And now we have user webdeveloper’s password in plaintext from Mongo DB! We can use “su webdeveloper” to switch users with our new password.
LOCAL RECON

We easily found our first flag, user.txt, in the /home/webdeveloper directory.
63—-omitted—---45
After uploading Linpeas to the target machine via a python3 simple HTTP server, let’s run it and analyze the results.

The first CVE is the one we will use to privesc. Instead of using the three file method that is outlined on exploit-db, we’ll do it manually using two terminals logged in as webuser.

Let’s also check sudo privileges.

The LD_PRELOAD and sky_backup_utility are both interesting findings. We’ll save these for later in case we hit a dead end with CVE 2021-4034.
PRIV-ESC

We’ll execute privilege escalation by exploiting a glitch in the pkexec bin (policykit vulnerability – cve-2021-4034). Open a second shell as webdeveloper.
Issue the following commands one-by-one in the corresponding terminals.
| Terminal 1 | Terminal 2 |
echo $$ |
|
pkttyagent --process <number of the process ID from echo $$> |
|
pkexec "/bin/bash" |
|
password for webdeveloper |
|
| (recieve the root shell in terminal 1) |
POST-EXPLOITATION
Let’s grab the root flag:

FINAL THOUGHTS

This box was fairly challenging and really pushed me to take careful notes about my findings during enumeration and also to thoughtfully plan my strategy for gaining the initial foothold and for the priv-esc stage.
These more advanced boxes are forcing me to start putting together longer sequences of hacking tricks that were used more in isolation on the easier boxes.
https://www.sickgaming.net/blog/2023/02/...challenge/


